top of page
ISO Consultancy
Amazon Supplier ISO Support
Independent ISO readiness and implementation support for Amazon sellers responding to accredited certification requirements.

Search

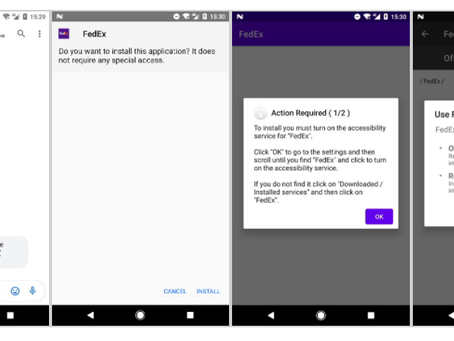
Take action now – FluBot malware may be on its way
Why FluBot is a major threat for Android users, how to avoid falling victim, and how to get rid of the malware if your device has already been compromised Android malware known as FluBot is continuing to cause mayhem across some European countries, and there is speculation that the threat actors behind it may decide to target other geographies, including the United Kingdom. Here’s why you should be vigilant, how FluBot operates, and how you can remove this Android nasty from

Scott Naisbett
3 min read


Cyber‐attacks set to become more targeted in 2021, according to HP Inc.
Cybersecurity predictions for 2021 show the ripple effect of COVID-19 is likely to continue, leading to a rise in thread hijacking, whaling and human-operated ransomware PALO ALTO, Calif., December 1, 2020 – HP today released its 2021 predictions on how security threats – such as human-operated ransomware, thread hijacking, unintentional insider threats, business email compromise and whaling attacks – are set to increase in the next 12 months. HP’s cybersecurity experts inclu

Scott Naisbett
6 min read


5 ways to prevent data breaches and cyber attacks
With media headlines focusing on household names like British Airways, Travelex, and Uber, it can be tempting to assume that cyber criminals only target big companies with deep pockets. But the truth is that six out of ten SMEs suffer cyber attacks , and a quarter of the UK’s charities suffered an attack in 2019 . So what can you do to protect your organisation against this kind of crime? Training Many organisations are not supporting their staff with the appropriate trainin

Scott Naisbett
4 min read


Why ISO 27001 is ‘the’ standard for information security
ISO 27001 is one of the fastest-growing management standards in the world, with certifications growing at an annual rate of 20%. If you have not already done so, it may be time to consider this standard for your organisation. ISO/IEC 27001:2013 (ISO 27001) is the international standard that describes best practice for an information security management system (ISMS). Achieving accredited certification to ISO 27001 demonstrates that your company is following information securi

Scott Naisbett
3 min read


Why The Largest Cyberattack In History Is Predicted to Happen Within Six Months
The Coronavirus Just Ripped Open Every Company’s Virtual Defences Before the pandemic hit, employees who worked remotely were usually given special work laptops with beefed up security and given strict guidelines that say they must only use a dedicated work laptop using a separate, secure wi-fi connection. They normally have to jump through multiple security hoops to even get past the welcome screen. For example, they must plug in a USB security stick to “unlock” work files.

Scott Naisbett
3 min read


Five Ways to Prevent Social Engineering Attacks
Social engineering is a growing field and with your users at your last line of defence, security teams ought to be mindful of each user’s activity to interfere if needed. However, as an end user, you have a responsibility yourself to monitor your own activities. Here are some tips and tricks to start. Some Quick Tips to Remember: Think before you click. Attackers employ a sense of urgency to make you act first and think later in phishing attacks. When you get a highly urgent

Scott Naisbett
3 min read


8 Ways Businesses Can Prevent Cyber Attacks
According to a defence outlook report by Deloitte, the wealthier the nation, the more at risk a country is of cyber attack. The US, Japan, Britain and South Korea have been identified as some of the biggest targets. Not to mention, the recent cyber attack on the federal government may have exposed as many as 4.2 million current and former federal employees including investigations for security clearances and other job background checks. Moreover, In a report sponsored by Inte

Scott Naisbett
4 min read


Does your use of CCTV comply with the GDPR?
You might be surprised to learn that CCTV footage is subject to the GDPR (General Data Protection Regulation). The Regulation isn’t just about written details, like names and addresses; it applies to any information that can identify someone. That includes pictures and videos, which is why you should be careful about the way you use CCTV. Let’s take a look at the steps you should follow to ensure your video surveillance methods are GDPR-compliant. 1. Make sure people know the

Scott Naisbett
5 min read


The world’s most valuable resource is no longer oil, but data
A NEW commodity spawns a lucrative, fast-growing industry, prompting antitrust regulators to step in to restrain those who control its flow. A century ago, the resource in question was oil. Now similar concerns are being raised by the giants that deal in data, the oil of the digital era. These titans—Alphabet (Google’s parent company), Amazon, Apple, Facebook and Microsoft—look unstoppable. They are the five most valuable listed firms in the world. Their profits are surging:

Scott Naisbett
1 min read


Myths Buster | Auditing
We spend a lot of time researching and listening to our clients and so called 'experts' in the field of ISO Standards and thought, well hoped that we could clarify a few things and help dispel many common miss-conceptions associated with the perception of auditing management systems. Myth 1; "The auditor is only interested in our procedures." Buster 1; A good auditor will be more interested in the process behind the procedures, how effective these are and how they have been

Billy Naisbett
2 min read


A guide to spotting and dealing with phishing emails
I've received a suspicious email Our guide to spotting and dealing with phishing emails If you haven't clicked any links in the email, that's good. Until you're certain that the sender is genuine, you should not follow any links, or reply. The next thing to do is try and identify whether the email is a scam, or genuine. Here's some tips on spotting phishing emails. Many phishing emails have poor grammar, punctuation and spelling. Is the design and overall quality what would

Scott Naisbett
2 min read


Are Your Employees Using Your Data in the Shadows?
You have superstar employees who run your business like it’s their own. They use new apps to collaborate with co-workers, vendors, and customers to get work done when it needs to get done. They’re moving your business closer and closer to the cloud. Sounds fantastic! Let them do their thing! But what information is being shared? What apps are they using? Are they secure? Are partners or customers receiving sensitive data that’s not encrypted? Here are a few things to keep in

Scott Naisbett
3 min read


What to consider in security terms and conditions for employees according to ISO 27001
A good way to ensure that people are aware of their roles and responsibilities in an organisation is by defining policies and procedures to be followed. But this solution has a limitation: they only cover the people who are already working for the organisation and have access to information. What do you do when you need to introduce new employees or contractors in the environment? Once the proper candidates have been selected by the organisation it is important to ensure the

Scott Naisbett
4 min read


GDPR - one year on
The Information Commissioner's Office have recently announced that the focus for year two of GDPR must be BEYOND baseline controls and compliance. It's time to get intricate. All businesses are expected to focus on accountability and demonstrate an understanding of the risks involved in the way they process data, and how those risks should be mitigated. With over 40,000 data complaints made over the past year and over 14,000 personal data breaches, they now have the necessa

Scott Naisbett
1 min read


Myths Buster | ISO 27001
We spend a lot of time researching and listening to our clients and so called 'experts' in the field of ISO Standards and thought, well hoped that we could clarify a few things and help dispel many common miss-conceptions associated with the ISO Standards. Myth 1; "ISO 27001 will require thousands of mandates, lots of money to invest in IT equipment and systems, and would take forever to get implemented.” Buster 1; The Standard is not as complicated as you might think and t

Scott Naisbett
4 min read
bottom of page
